In an increasingly interconnected world, cybersecurity has become a top priority for businesses and industries. With the rise of the Industrial Internet of Things (IIoT), automation, and process digitalization, industrial networks have evolved from closed environments to ones exposed to new cyber threats.
Among these threats, the Man-in-the-Middle (MiTM) attack stands out as a significant risk to the integrity and confidentiality of industrial communications. In this article, we will examine MiTM attacks in detail, explore effective prevention measures, and demonstrate how InprOTech Guardian – our advanced security solution for industrial environments – detects and mitigates these threats through a real-world use case.
What is a MitM Attack?
A Man-in-the-Middle (MiTM) attack is a type of cyberattack where an attacker stealthily positions themselves between two communicating parties, intercepting and potentially manipulating the exchanged data without their knowledge. These attacks can have severe consequences, such as credential theft, data manipulation, industrial process disruption, and sabotage of critical infrastructures. By significantly compromising data confidentiality and integrity, MiTM attacks pose a severe threat to the exchange of sensitive information.
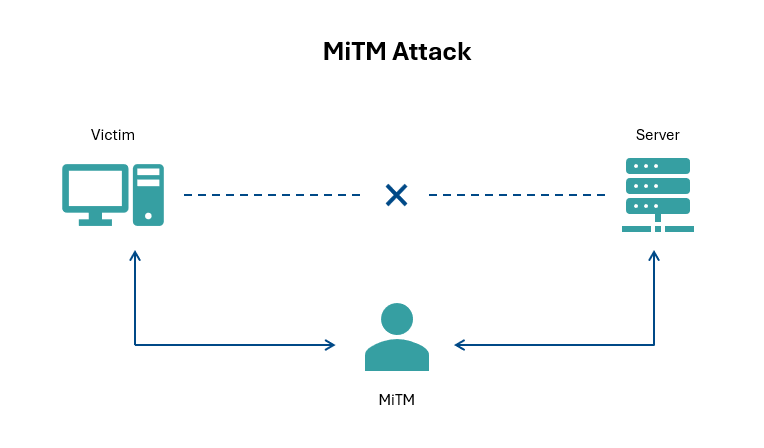
How Does a MiTM Attack Work?
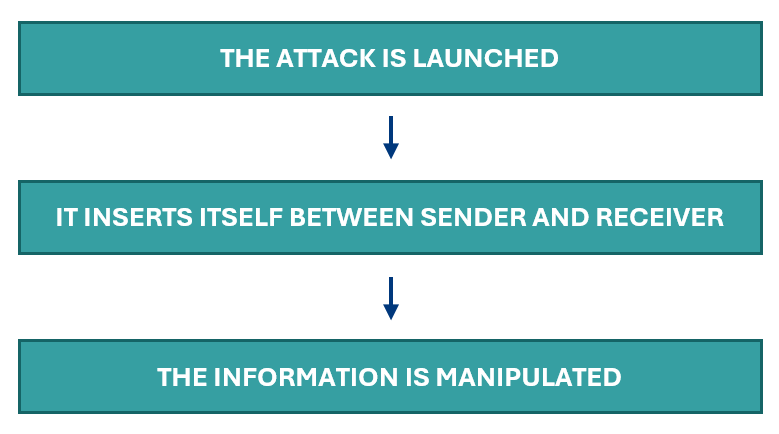
A MiTM attack typically unfolds in two key phases:
Interception of information
The attacker must insert themselves into the communication flow between the victim and the target server. To achieve this, they can use various techniques depending on the environment:
- Local Network Interception:
- Devices use the Address Resolution Protocol (ARP) to associate IP addresses with MAC addresses. Attackers can send fake ARP responses to link their MAC address to the gateway’s IP, causing all traffic from the victim to pass through the attacker before reaching its real destination.
- ND Spoofing (on IPv6 networks): Similar to ARP Spoofing but applied to IPv6, exploiting the Neighbor Discovery Protocol (NDP) to intercept communications.
- Wireless Network Interception:
- Rogue Access Point (Fake WiFi Access Point): Attackers set up a malicious WiFi network with a name similar to a legitimate one, tricking users into connecting. Once connected, all their data is intercepted.
- Evil Twin Attack: A fraudulent WiFi access point with the same SSID as a trusted network is created. Devices automatically connect to it without detecting the switch, allowing attackers to capture and manipulate traffic.
- Server Spoofing Interception:
- DNS Spoofing (Cache Poisoning): The attacker manipulates DNS responses to redirect victims to fake websites that mimic legitimate ones (e.g., banking, social media sites) to steal credentials.
-
- HTTPS Spoofing: Users are deceived into trusting fake SSL/TLS certificates, allowing attackers to intercept and modify encrypted traffic. This can be done through self-signed certificates, attacks on Certification Authorities (CAs), or exploiting TLS implementation vulnerabilities.
Manipulation of Information
Once the attacker has successfully intercepted communication, they gain the ability to analyze, modify, and even inject malicious data into the traffic. Depending on their objectives and the type of intercepted communication, attackers can:
- Interception and extraction of critical data: One of the most common objectives is the theft of critical data, allowing the attacker to monitor industrial processes in real-time, extract access credentials for SCADA/ICS systems, and even steal production data, sensor statuses, or critical equipment configurations.
- Modification of data in transit: Attackers can alter transmitted information. If they successfully manipulate communication between a PLC and an HMI, they may change critical values without the operator noticing, leading to severe consequences such as tampering with safety parameters in production lines, altering alarms, modifying operational commands, etc.
- Injection of malicious content: Attackers can inject malicious code into industrial communications, which could lead to malware infiltration in SCADA servers, traffic redirection to fraudulent sites or creation of new backdoors for deeper network penetration.
- Session Hijacking: Some attackers may exploit this phase of the MiTM attack to perform session hijacking, a technique that allows them to take control of the victim’s active session and continue interacting with the system as if they were the legitimate user. This enables them to intercept and reuse active sessions on ICS/SCADA platforms, potentially leading to unauthorized access to operator interfaces (HMIs) and workstations, execution of malicious commands with elevated privileges or impersonation of administrators or maintenance technicians.
As we have seen, MitM attacks in industrial environments pose a severe risk as they can allow attackers to intercept, manipulate, or take control of automation systems. This can result in production failures, machinery sabotage, operational data loss, or even physical or human damage. To minimize these risks, it is essential to implement specific security measures for industrial networks, SCADA systems, and IoT devices.
Securing Industrial and Automation Networks
Industrial plants often operate with private internal networks, but if they are not properly protected, they can be vulnerable to MitM attacks. To reduce risk, the following key measures should be implemented:
- Network Segmentation and VLANs:
-
- Separate the production network from the administrative network to prevent unauthorized access.
- Implement industrial firewalls and Access Control Lists (ACLs) to restrict communication between critical devices.
- Using VPNs and Encrypted Remote Connections:
- Use strongly encrypted VPNs for remote access to industrial systems.
- Avoid direct connections to PLCs and SCADA systems from the Internet without additional security.
- Traffic Monitoring and Anomaly Detection:
- Deploy Intrusion Detection (IDS) and Prevention (IPS) Systems to identify suspicious traffic.
- Analyze network logs for spoofed ARP packets or suspicious DNS redirections.
Protection Against Attacks on Industrial Protocols (SCADA, PLCs, IoT)
Many industrial communication protocols such as Modbus, DNP3, OPC-UA, and Profinet were not designed with built-in security, making them vulnerable to MitM attacks if not properly secured.
- Enable Encryption in Communication Protocols:
-
- Use secure versions of industrial protocols, such as Modbus/TCP with TLS or OPC-UA with encryption and authentication.
- Configure IPsec or internal VPNs to encrypt communication between PLCs and SCADA systems.
- Implement Strong Authentication in Industrial Devices:
- Enforce two-factor authentication (2FA) for SCADA workstations and administration consoles.
- Avoid using default passwords on PLCs and HMIs.
- Disable Insecure Protocols and Limit Access:
- Block unnecessary services that lack encryption, as they can be exploited in MitM attacks.
- Apply IP whitelisting to restrict which devices can communicate with critical systems.
Protection Against Session Hijacking and Data Manipulation
Attackers can leverage a MitM attack to hijack active sessions in SCADA systems, modify control commands, or alter operational parameters. To mitigate this risk, follow these recommendations:
- Use Secure Session Tokens and Authentication in SCADA
-
- Implement short-lived session tokens with frequent regeneration to prevent reuse in session hijacking attacks.
- Configure session cookies with the Secure, HttpOnly, and SameSite flags to prevent unauthorized access.
- Real-Time Monitoring and Alerts
- Set up alerts to detect unexpected changes in the operational values of PLCs.
- Log suspicious activity in SCADA systems and generate periodic audit reports.
- Avoid Unencrypted Access to Control Systems
- Never access SCADA platforms from public or unprotected WiFi networks without using a VPN.
- Configure industrial firewalls to block suspicious connections or unauthorized access attempts.
Staff Training and Best Security Practices
One of the biggest risks in an industrial environment is human error. Many MitM attacks begin due to misconfigurations, weak passwords, or access to insecure networks. To strengthen security, follow these recommendations:
- Train Employees in Industrial Cybersecurity
-
- Teach operators and technicians how to identify MitM and phishing attacks.
- Conduct attack simulations to test personnel’s response capabilities.
- Enforce Strict Access Control Policies
- Implementar principios de mínimos privilegios (Least Privilege Access) para que solo personal autorizado pueda acceder a sistemas críticos.
- Utilizar tarjetas inteligentes o autenticación biométrica para acceder a entornos industriales sensibles.
- Regular Audits and Security Testing
- Conduct industrial penetration tests (pentesting) to assess the security of production networks.
- Keep all security software in firewalls, routers, and control devices up to date.
InprOTech Guardian
InprOTech Guardian is an advanced cybersecurity tool specifically designed to protect industrial networks. Its primary objective is to monitor traffic in production environments and analyze it using a combination of static rules, an IDS (Intrusion Detection System), artificial intelligence, and a honeypot. This approach enables the efficient identification of threats and the generation of real-time alerts, directly notifying plant managers and operators about potential attacks or operational failures, thus facilitating a quick response and minimizing impact.
The powerful threat detection system of InprOTech Guardian makes it an ideal solution for protecting industrial infrastructures against MitM attacks, thanks to its multi-layered security approach, which includes:
- Static rule-based detection, designed by the InprOTech team to identify common attack patterns in industrial environments.
- Detection through ML/AI algorithms, which analyze network behavior and traffic to identify anomalies and unknown threats.
- Signature-based detection via an IDS, incorporating third-party and community signatures to detect known attacks.
- Integration of a low-interaction honeypot, acting as a decoy to attract attackers and detect them before they compromise critical systems.
In addition to its threat detection capabilities, InprOTech Guardian offers key functionalities for cybersecurity management and strategy in industrial environments, including:
- Real-time traffic monitoring.
- Automated inventory of devices connected to the network.
- Customization of the tool to adapt to the company’s needs.
- Vulnerability analysis to identify weak points in the infrastructure.
- Blocking traffic from malicious IP addresses.
- Periodic report generation to facilitate strategic decision-making.
With these capabilities, InprOTech Guardian not only enhances the security of industrial networks but also optimizes threat management and response, ensuring a safer and more resilient environment.
Use Case: InprOTech Guardian vs. a MitM Attack
Simulated Attack in a Virtual Factory
To demonstrate InprOTech Guardian’s detection and response capabilities against a MitM attack, a simulation was conducted in a virtual beverage factory.
Before the attack, the asset panel and network map displayed only authorized devices, previously validated by the operator. However, once the attack begins, a malicious node infiltrates the network and starts communicating with two legitimate devices, positioning itself between them to intercept traffic.
InprOTech Guardian immediately detects the anomaly and generates real-time alerts, notifying about:
- The establishment of a suspicious new connection between the affected devices and the attacker.
- The detection of an ARP spoofing attack, in which the attacker manipulates MAC-IP assignments to intercept communication.
- The identification of a new IP associated with the attacker’s device.
Thanks to its fast detection capabilities, InprOTech Guardian allows proactive action, mitigating the attack’s impact and reinforcing the security of the industrial network.
Real-Time Monitoring and Rapid Response
Through continuous monitoring, InprOTech Guardian not only identifies the attacker’s presence but also allows visualization of their exact location within the network. In the network map, the malicious node’s interactions with other devices can be observed, enabling the security team to take immediate action to contain the threat.
Mitigation Measures
Once the attack has been detected, operators can:
- Isolate the suspicious node from the network to prevent data manipulation.
- Block communication between the attacker and critical devices.
- Apply network segmentation to prevent unauthorized devices from interacting with sensitive systems.
- Update access and authentication rules to strengthen the security of the industrial network.
InprOTech: Your Cybersecurity Ally for Industrial Environments
To tackle challenges like MitM attacks, InprOTech provides advanced cybersecurity solutions specifically designed to protect industrial environments.
InprOTech Guardian enables industrial companies to monitor their networks in real time, detect anomalies proactively, and prevent various types of attacks against industrial environments. Additionally, our security auditing and consulting services help strengthen the technological infrastructure of factories, reducing the attack surface and ensuring comprehensive protection against advanced threats.
If you’re interested in our assistance, you can contact us by clicking here.



