Last Wednesday 14th, our CEO Iago Fortes attended as a speaker at the “Obradoiro Technologies and Systems 4.0: “Data” for better decision making”. As always, we will tell you about the topics that have been discussed in the different presentations, and of course, some conclusions.
SPEECH CARLOS PRIETO (RIA21) – “YOU ARE THEIR TARGET”
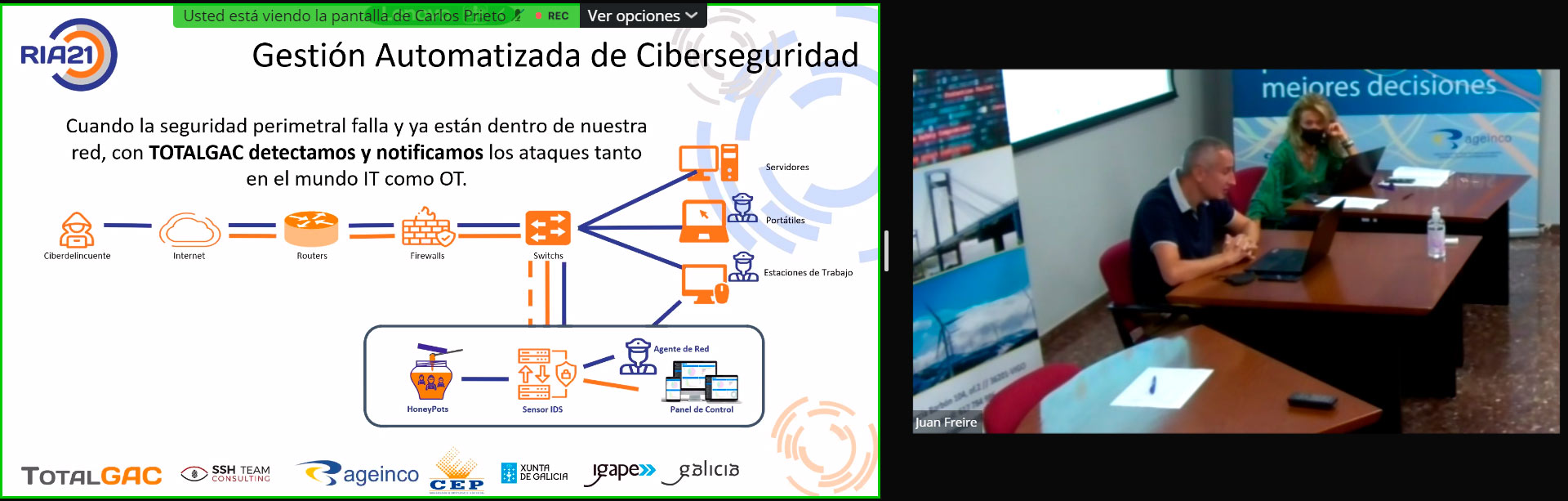
The first presentation began at 10:30 with Carlos Prieto from RIA21 as the protagonist. Under the title “If you are their target, they are targeting you or they will attack you”, Carlos analyzed several topics among which we highlight.
- A brief explanation of the evolution of society.
- CID (Confidentiality, Integrity and Availability). Processes and products.
- Information flow and vulnerabilities.
- Good practices for each of the main risks such as: safe surfing, not leaving devices to children, unknown links (URLs), WiFi, USBs.
- Presentation of RIO21 and the origin and history of the SSH Team matrix.
- Presentation of TotalGAC (Neotec project).
PRESENTATION IAGO FORTES (INPROTECH) – “THE FACTORY CANNOT STOP”
After Carlos’ presentation, it was Iago Fortes’ turn to explain our experience in industrial cybersecurity under the title “The factory cannot stop”. We highlight the following aspects of the presentation:
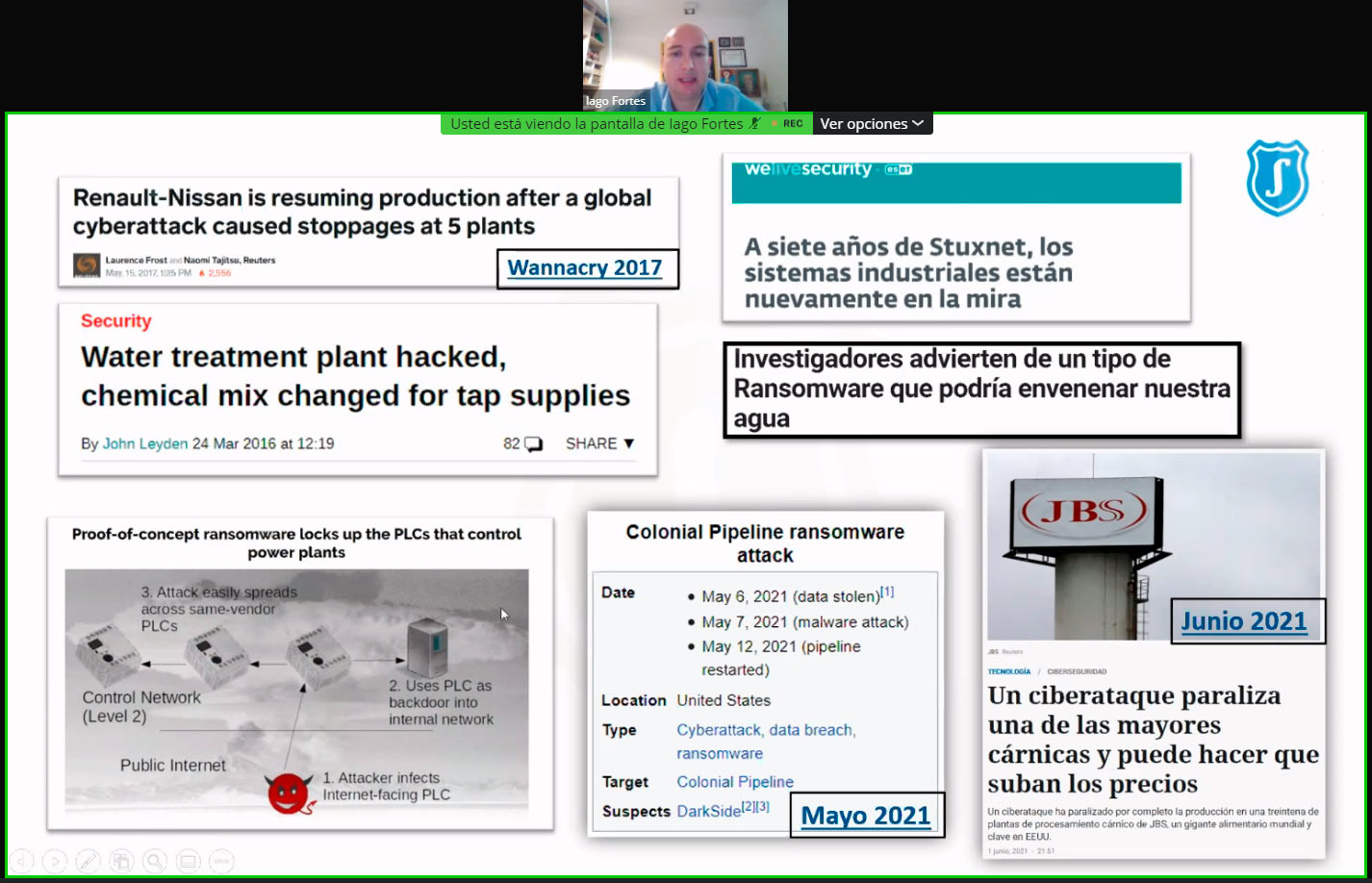
- Explanation of recent and historical cases of industrial cybersecurity.
- Stuxnet case: the first attack targeting industry and the OT world and the first cyber-weapon.
- Problems and risks and main vulnerabilities in the OT world (the 7 most important): Passwords/default/weak configuration, lack of network segregation, insecure OT protocols, out-of-date systems,…
- Solutions: Areas of action and the most important strategies and areas.
- Solutions, including InprOTech Guardian
- Presentation of the Inprosec group, and the specialized InprOTech line, including customer references.
PRESENTATION PILAR VILA (FORENSICS AND SECURITY) – “WHAT HAPPENS WHEN EVERYTHING GOES WRONG”
The presentation by Pilar Vila from Forensics and Security under the title “What happens when everything fails” explained different aspects from her point of view:
- Risk Management.
- The challenge and problem of BYOD: Bring Your Own Device.
- The importance of policies and legal compliance, signed and agreed with the employee and user.
- Detail of the forensic analysis: The “computer forensic” and its legal function.
- Objective, Process, Standards, Criteria, etc.
- Common examples: Unfair competition, also usually from the work team (and from the corporate account the information is forwarded to their other accounts).
- Formatting and storage.
- Commitment and guarantees that access is only to what is necessary (according to scope) and nothing more.
- Presentation of the company and solutions: Changes following COVID-19 and greater choice (on the part of the client) to be more proactive, rather than so reactive.
- Now even “preventive” forensic analysis is often done to verify if there is a problem/malware already resident.
JORGE CEBREIROS (INFOJC) – “SECURE COMMUNICATIONS IN TELEWORK AND MOBILITY ENVIRONMENT”
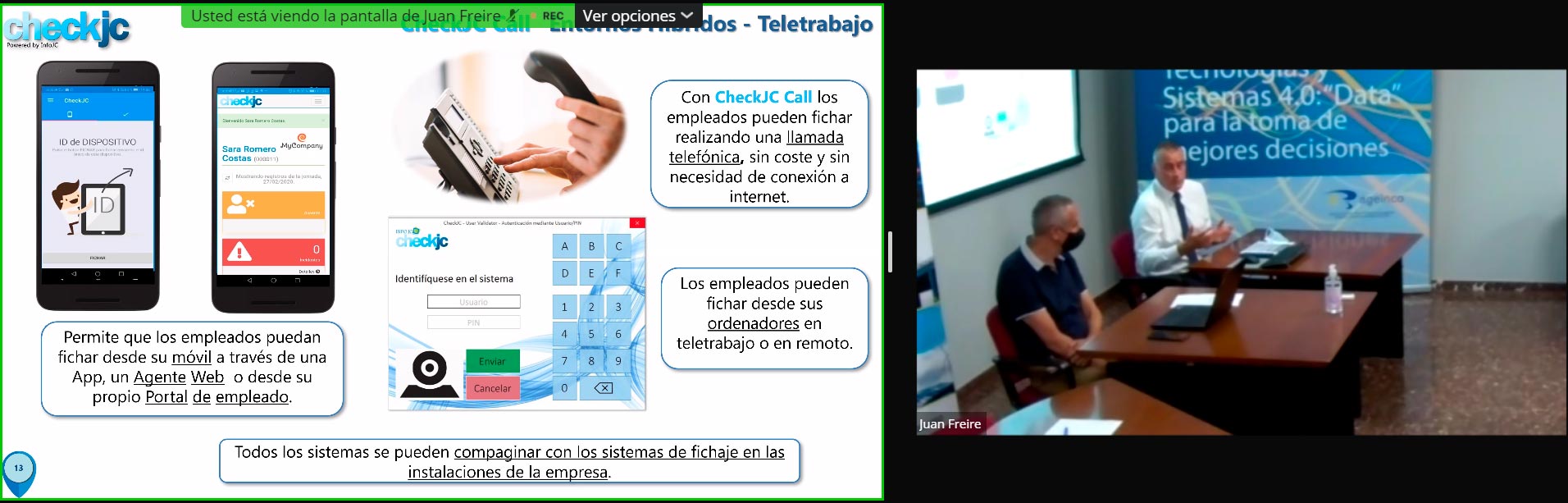
The last presentation of the day was by Jorge Cebreiros of INFOJC, exposing his vision on secure communications in a new situation for many: teleworking. He presented:
- An introduction to CheckJC and Security by Design.
- The challenge and problem of BYOD: Bring Your Own Device.
- Security in architecture and data storage.
- Authentication security – avoiding impersonation.
- Access Management: Roles and Permissions.
- Remote and Mobile Access: VPN, Security, Communications.
- Legal security and validity of information and as evidence.
CONCLUSIONS
Once the presentations were finished, a summary was made and a summary of all the interventions was shared, from which the following conclusions can be drawn:
- Manage security from the design, from the beginning and proactively.
- Do it in a transversal way, in any area, in any project, etc.
- Keep in mind that risk and cybersecurity management is necessary for all types of companies, from the largest to the smallest.
- Take advantage of the specific and additional funding that has already arrived and that will arrive in the next months and year and a half (Next. Gen. funds) especially aimed at SMEs and Cybersecurity.