The horizon of the digital transformation of the industrial sector, Industry 4.0, is the integration of industrial control and production systems (OT, Operational Technology) with information technologies (IT, Information Technology). This convergence can generate enormous operational benefits, but it also exposes potentially critical infrastructures to all the well-known cybersecurity vulnerabilities, for which defense or mitigation mechanisms are not always applicable. This risk is part of a broader challenge, as the two domains being integrated in this process have different natures (arguably complementary in many aspects): in industrial plants, the priority will always be availability and physical safety; they are not designed for regular update or patching routines; communication with network components does not always rely on open protocols; and a long list of differences separates both worlds1,2.
To protect industrial environments, it is essential to collect and observe network traffic. In this context, InprOTech Guardian, our real-time industrial network monitoring solution, enables continuous and non-intrusive analysis of industrial network traffic, facilitating early detection of anomalies, unauthorized behaviors, operational failures, and potential cybersecurity incidents, while also providing visibility into connected assets, vulnerabilities in deployed services, and normal communication patterns. To adapt to different environments and operational requirements, InprOTech Guardian3 can collect traffic using two technologies available in the industry: Port Mirroring (also known as SPAN, Switched Port Analyzer) and TAPs (Test Access Points)4.
This article provides an overview of what they are, how they work, their advantages and disadvantages, and which is more suitable depending on the industrial context.
Port Mirroring – SPAN
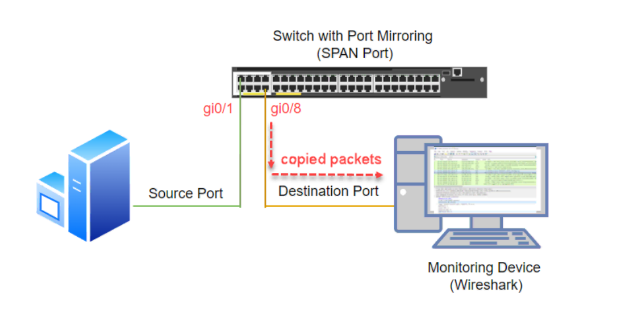
Port Mirroring is a technology available in many switches and network devices that allows traffic from one or more ports or VLANs to be replicated to another port, known as the mirror port, where it can be analyzed.
Typically, an administrator specifies the source port(s) to be duplicated and a destination port from which the traffic can be read. Nowadays, this is a basic feature that can be easily configured through the switch’s web management interface. Some vendors also include options to filter traffic before it is sent, as well as more advanced features such as RSPAN (Remote SPAN, meaning traffic duplication from one switch to another within the network)5.
Advantages of Port Mirroring
- Low cost: does not require additional hardware beyond the switch.
- Flexible: multiple ports or VLANs can be selected.
- Remote configuration: can be changed via software without physical access to cables.
Disadvantages of Port Mirroring
- Packet loss: In high-traffic situations, the switch may not copy all packets. In addition, the mirror port may become saturated and drop data.
- Impact on switch performance: Some implementations degrade switch performance during mirroring.
- Limited visibility: Traffic that does not traverse the switch cannot be observed. It does not capture physical traffic between devices that do not pass through the mirrored ports.
TAPs (Test Access Point)
The taps have a long history dating back to the invention of the telegraph, with a general definition as a small device that can be attached to a communication system, such as a telephone, to secretly listen to communications. However, in the world of telecommunications and cybersecurity, this definition has evolved to refer to a physical hardware component inserted into a network link to split the traffic flow and send an exact copy to an analysis tool without interfering with the original traffic. In this redefinition process, the term has become the acronym Test Access Point6.
Since the emergence of the first network TAPs, communications technology has evolved significantly: speeds have increased, new protocols have emerged, and high-speed fiber optics have become the standard.
At the same time, organizations increasingly need to deploy security and monitoring tools to protect their digital assets, ensure service continuity, and improve user experience.

Types of TAPs
As a result, network TAP technology has also evolved and now offers multiple operating modes that should be considered when designing a reliable and resilient connectivity architecture7. Functionally, they can be classified as:
- Breakout “Normal” TAPs: Traffic copying and forwarding to monitoring tools has high priority to ensure no packet loss.
- Filtering TAPs: Establish traffic filtering rules before traffic reaches monitoring tools.
- Aggregation TAPs: Combine traffic from different sources.
- Replication TAPs: Create multiple copies of traffic data so that several devices can read from different points in the network.
- Bypass TAPs: Prevent network outages caused by devices in case of failure or when maintenance and updates are required.
- Media Changing TAPs: Ensure compatibility between networks and connected devices when technology changes or upgrades occur.
Advantages of TAPs
- Complete traffic capture: No packet loss due to capture device saturation. Exact physical frames are obtained, including collisions or errors.
- No impact on network performance: Being passive, it introduces no latency and does not alter traffic.
- Higher reliability: It is a more attractive solution for critical industrial monitoring, as mentioned earlier, since there are TAPs that maintain connectivity even if they lose power (by-pass).
- Deep visibility: Allows capturing traffic that does not pass through smart switches or complex VLANs.
Disadvantages of TAPs
- Cost: Additional physical devices that can become expensive depending on the installation, especially when deployed across many links.
- Physical installation: Requires access to cabling and may involve brief service interruptions.
- Management and expertise: Requires planning of monitoring ports and analysis. Compared to enabling port mirroring, it demands a higher level of knowledge about the different types and models, which is often limited to manufacturers and partners.
Summary
In summary, both TAPs and port mirroring provide visibility into industrial network traffic, but they address different needs and contexts. Port mirroring stands out for its ease of deployment and low cost, leveraging the capabilities of the switch itself, making it suitable for environments with lower traffic volumes or for occasional analysis; however, its dependence on network device performance can lead to packet loss and incomplete visibility in demanding scenarios. TAPs, on the other hand, offer passive, continuous, and faithful traffic capture without impacting the network or production devices, making them the most robust and reliable option for critical industrial environments where availability and analytical accuracy are priorities. In practice, the choice between one or the other—or even a combined approach—depends on the desired balance between cost, ease of deployment, and required level of visibility.
Both methods are used by InprOTech Guardian to passively capture industrial traffic and perform all necessary monitoring and analysis tasks to prevent, mitigate, and investigate potential issues and attacks.
References
[1] https://www.incibe.es/en/incibe-cert/blog/itot-convergence
[2] Security of IT/OT Convergence: Design and Implementation Challenges. B. Zahran et al.: https://arxiv.org/pdf/2302.09426
[3] https://inprotech.es/guardian/
[4] https://learn.microsoft.com/en-us/azure/defender-for-iot/organizations/best-practices/traffic-mirroring-methods
[5] SPAN (and RSPAN) is CISCO terminology, the first to incorporate port mirroring into their switches.
[6] Technically, this would be a retronym: https://es.wikipedia.org/wiki/Retroacr%C3%B3nimo
[7] https://www.garlandtechnology.com/wpi-network-taps-101


