A vulnerability scanner is a piece of software whose role is to make an inventory of assets within a network, and to carry out more or less automated probes within these to detect vulnerable applications, resources or systems. It is, therefore, a non- negotiable part of the secure software development life cycle (SDLC)a. An authoritative definition of vulnerability, in the context of software development, is that given by the American National Institute of Standards and Technology, NIST:
«A weakness in the computational logic (for example, in the code itself) of software and hardware components that, if exploited, would lead to a negative impact on confidentiality, integrity or availability. Mitigation of vulnerabilities in this context typically involves code reviews, but also changes in specifications or discontinuities (such as the withdrawal of entire protocols or functionalities)»b.
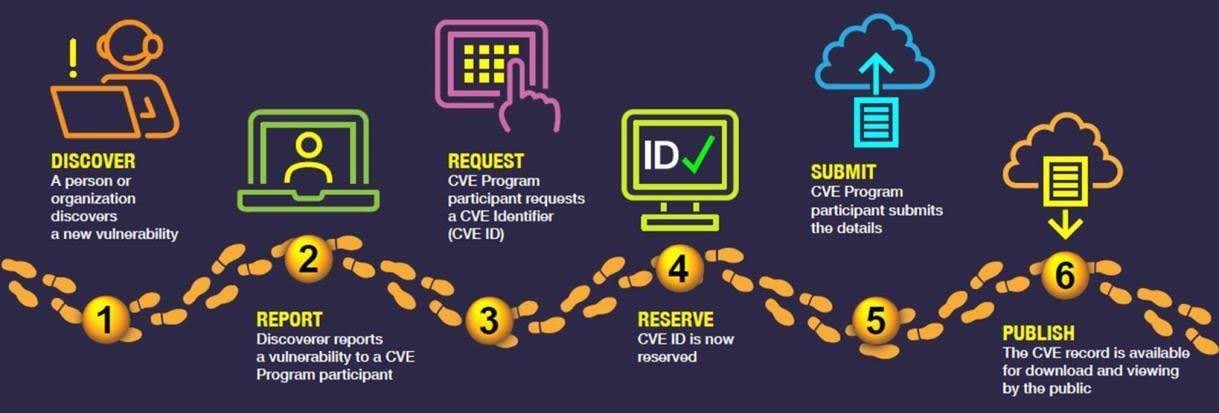
Software development is a strongly community-oriented enterprise: much of the code written is produced with a public service vocation, and contains or uses code written by others. It is therefore desirable to maintain a publicly accessible, professionally curated list of all detected vulnerabilities, a task undertaken by the US in its role as the technological power of the 20th century. In 1999, MITRE, a non-profit corporation funded by several federal research and development centers, inaugurated the CVE (Common Vulnerabilities and Exposures) List. CVEs follow a naming
system to uniquely identify a given vulnerability, which has the form CVE- 2022-001122. They also have a standardized publication system, or life cycle, that goes from the discovery of the vulnerability by a user to its publication on the listc. Years later, in 2005, NIST launched the NVD (National Vulnerability Database) with the idea of enriching the CVE List with additional information such as a numerical score of the vulnerability risk or the availability of patches. This standardization of vulnerabilities helps to promote the use of scanners, as it establishes a common language and confidence in the process.
Both IT (Information Technology) and OT (Operational Technology) networks, where industrial networks would be found, need acceptable security standards to maintain their long-term operability, but their different nature means that the tools appropriate for one are not appropriate for the other. In addition to the fact that the protocols used in internal communications are usually different, the priorities to be maintained are very different in both cases: in industrial environments it is essential to maintain the continuity of production and any interruption in communications or availability of any node in the network can cause global shutdowns. This means that scans have to be carried out with much more care than in an IT network, where occasional downtime is accepted as normal.
Given the importance of having a specific vulnerability management tool in the context of OT networks, at InprOTech we have developed tools to conveniently equip our InprOTech Guardian monitoring solution.
InprOTech Guardiand is a cybersecurity tool designed and developed for industrial networks. Its main function is to monitor the traffic generated by the factory and analyse it based on a combination of static, community and AI-powered rules, from which alerts can be deployed directly to plant managers and/or operators and thus cut off any attack or malfunction that may be occurring. In addition to these main capabilities, InprOTech Guardian also offers its own vulnerability scanner, which allows them to be detected, visualised and managed in a comprehensive manner.
Development
A vulnerability scanner should be able, in general terms, to (1) obtain a list of the assets in the network, (2) detect vulnerabilities in them, (3) classify them and provide relevant information about them, (4) generate reports and statistics, and (5) manage these vulnerabilities. Below, we discuss these points in more detail, focusing on our approach:
- Scanning assets in the network: lists the devices present in an environment. This is one of the core functionalities of InprOTech Guardian, which allows obtaining an enriched inventory of the nodes present in the network in real time. In addition, administrators and operators can mark some devices based on their criticality for the operation of the network (critical devices will not be scanned to avoid possible interruptions or alterations).
- Vulnerability detection: obtains information about the open services and ports, operating systems, firmware, installed on said non-critical assets. Using CPE (Common Platform Enumeration) tags, another standard that identifies software products plus their version, it obtains information on existing vulnerabilities from public databases such as NVD.
- Classification and intelligence: enriches the previous search with extra information that allows you to classify vulnerabilities by severity, a summary that explains the nature of the vulnerability in a few lines, and links to further investigate possible mitigations.
- Generation of reports and statistics: transfers all this data to a format that is easy for a human to read and process. Specifically, a list in csv format with the list of vulnerabilities and their most important properties, and in the application itself, general statistics (scan coverage, number of vulnerabilities by severity and general risk levels…), as well as those focused on the devices.
- Vulnerability management: the user can manage the status of the different vulnerabilities: active, resolved, silenced or false positive. Inaddition, in the short term we will provide InprOTech Guardian with the ability to, using the valuable information provided by the vulnerability scanner, communicate with the network firewall to report the need to block certain connections in the event that a critical risk is detected.
There are very mature solutions on the market that also offer these services from the great dominators in the field of cybersecurity, such as Nessus, Tenable’s OT scanner, or OpenVAS, from Greenbone. These two options dominate a large part of the market, but they are more focused on clients with sufficient size to have dedicated teams, capable of handling these very powerful but also complex tools with ease.
InprOTech Guardian offers the possibility of integrating the results of an external vulnerability scanner, for the moment with compatibility with Nessus and OpenVAS.
Benefits
Although they have been discussed more or less extensively throughout this article, let us highlight the strengths of InprOTech Guardian’s Smart View as a vulnerability scanner:
- Asset control: to identify them, appropriately segment networks, discover inconsistencies between the network design in theory and in the factory itself.
- Risk identification: even when the vulnerabilities detected are not critical, attacking and resolving them can lead to an improvement in code quality.
- Threat mitigation: in cybersecurity, you can never be confident of having an impregnable network, but you should aim to discover as many weak points as possible, in order to later calculate whether it is worth mitigating them.
- Regulatory compliance: ensuring that the systems running on the network are free of known vulnerabilities is an important step towards compliance with European laws and directives (such as NIS2, which will come into force in October of this year 2024).
- Affordable and customized solution: Since our target customers are small and medium-sized companies that have decided to take the cybersecurity of their industrial environments seriously, the service we offer with InprOTech Guardian is one of direct communication and flexibility to adapt the product to the needs and preferences of the client. In addition, by focusing on the most central points of what a vulnerability scanner needs, we can adjust the cost of the service.
Why InprOTech Guardian?
✦ Simple to use and intuitive web interface. For any user, whether skilled or not. Really.
✦ Affordable. For any customer segment and company.
✦ Flexible. Our services come in many flavors, directly acting as vendor or service provider, or through partnerships with 3rd parties.
✦ Customizable. We work with our customers to develop new use cases and features.
✦ Geostrategically compliant. 100% EU made (R&D, development and support), giving EU-customers confidence in supply chain compliance.
✦ Agility. We care, and we work quickly.
Summary
In conclusion, the development of Smart View in InprOTech Guardian covers the need for a vulnerability scanner that allows obtaining reliable information and management options for them for industrial networks. It combines the power of both public databases, which contain all the relevant information, and the import of external vulnerability scanners, with the flexibility of customizing the query parameters and the assets to be scanned.
Resources
[a]www.redhat.com/es/topics/security/soft ware-development-lifecycle-security
[c]https://www.cve.org/About/Process#CV ERecordLifecycle



