The DNP3 Protocol is an industrial communication protocol used between components in process automation systems. It was developed for communication between several types of control and data acquisition devices. It is a protocol with critical functions and security vulnerabilities.
In order to avoid security breaches in the communication of ICS (Industrial Control Systems) infrastructures, this document lists the different security issues of the protocol, a secure authentication standard for DNP3 and provides recommendations to avoid security flaws.
Introduction
Until a few years ago, security in ICS (Industrial Control Systems) was not an issue, but in recent years, ICS have become one of the main targets of attack, making security a really important issue.
DNP3 is an industrial protocol for communications between intelligent equipment (IED) and controller stations, components of SCADA systems. It is a protocol widely used in the electrical sector with great popularity in the United States and Canada. It is less popular in Europe due to the use of alternatives such as IEC-60870 101 and IEC-60870 104.
DNP3 has some security challenges that may compromise confidentiality, authenticity, and integrity of messages.
This article will present the main features of the DNP3 protocol, its main functions, some of the protocol’s risk factors and security recommendations for a more secure implementation.
What are ICS?
Industrial control systems are devices, systems, networks, and controllers used to operate and/or automate industrial processes. They are increasingly exposed to interaction with other systems in the internet environment and have become a major target for attacks.
What is the DNP3 protocol?
The DNP3 Protocol is an industrial protocol for communications between intelligent equipment and control stations, components of SCADA systems.
DNP3 has several functionalities that make it a more robust, efficient, and compatible protocol than other older protocols such as Modbus. It is also a more complex protocol.
It is a three-layer protocol according to the OSI MODEL:
- Link layer
- Application layer
- Transport layer also called pseudo-transport layer as it does not comply with all specifications of the OSI model.
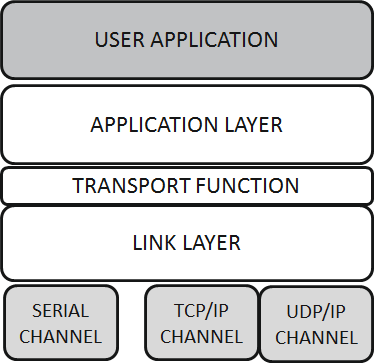
The frame format used is based on the FT3 as defined in the IEC 608770-5 specifications and makes use of the cyclic redundancy check (CRC) for error detection.
DNP3 data types
DNP3 information is categorised into four basic types:
- Binary inputs.
- Binary output.
- Analogue input.
- Analogue output.
Two more types are added to these basic types:
- Counters.
- Double binary input
Each DNP3 data item is called a point and is identified by an index. The current value of the data is called the static value.
The point can generate events on value changes or on receipt of commands. These events can be classified as class 1, class 2 or class 3 events.
The DNP3 data model is based on an object schema. Some of the most common objects used in DNP3 communications are:
- Object 1 – Digital Inputs: Allows the reading of digital inputs.
- Object 2 – Digital inputs events.
- Object 20 – Meters: This object allows the reading or manipulation of meters.
Binding layer
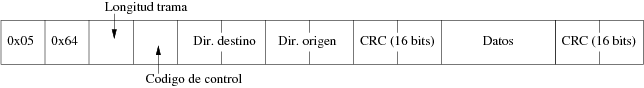
Link level messages in DNP3 are called frames and the maximum called frames and the maximum frame size is 292 bytes.
The link layer is responsible for addressing and error detection (CRC) tasks.
A DNP3 frame consists of three blocks:
- Header
- Data
- CRC
Transport Layer
Messages at the transport layer level are called segments. The maximum size of segments is 149 bytes.
The function of the transport layer is to allow single, structured messages in multiple frames and multiple fragments.
This layer chunks the fragments received via the application layer and adds the transport header and assembles at the receiving end the frames received through the application layer.
Application layer
Messages at the application level are called Fragments. The maximum size of a fragment is set to 1024 bytes.
The application layer is responsible for processing the fragments received from the transport layer. fragments received from the transport layer.
This layer defines functions that are exchanged between remote stations and controllers. Some of these functions are:
1:READ: Reading static value or events.
2: WRITE: Writing attributes of the equipment.
3:SELECT: Selection control service.
4:OPERATE: Order after selection.
5:DIRECT_OPERATE: Direct order without selection.
7:IMMED_FREEZE: Immediate freeze order.
9:FREEZE_CLEAR: Freeze and reset to 0.
13:COLD_RESTART: Total reset of the remote station.
14:WARM_RESTART: Partial reset of remote station.
20: ENABLE_UNSOLICITED: Used in modern remote stations to activate spontaneous sending.
21: DISABLE_UNSOLICITED: Used on modern remote stations to disable spontaneous sending. If disabled, the collection reading is done by class 1, 2 and 3.
22: ASSIGN_CLASS: Allows to assign to each point or point type a class for the events it generates. Usually, the remote station already organizes them, but this service, if implemented, allows the master to change this order.
Safety and critical factors
DNP3 is a protocol that is focused on the system availability and neglects other factors such as confidentiality and data integrity. It is an unencrypted protocol [3].
At the link layer level, are included typical link layer functions such as error detection via the CRC (which is not a security security measure since anyone modifying the frames will be able to change the CRC), but not any additional measures that ethernet does not offer.
At the application level there is a standard for secure authentication [1]. This standard provides authentication, integrity and confidentiality and solves the problems of:
- Impersonation.
- Message modification.
- Traffic re-injection attacks.
- Eavesdropping.
The DNP3 protocol allows to carry out several functions that have been discussed in the previous section. Some of these functions may be critical. The critical DNP3 functions are: write, operate, direct operate, direct operate no ack, cold_restart, warm_restart, abort and stop application.
Security suggestions
In order to improve the security of communications over the DNP3 protocol will be recommended:
- Monitor non-DNP3 communications on TCP/UDP 20000 ports.
- Pay particular attention to critical functions.
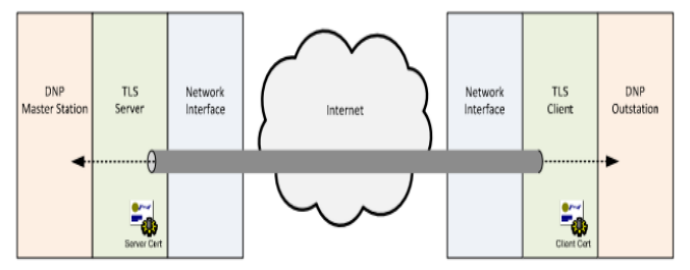
- Use the secure version of DNP3 whenever possible. If the use of this version is not possible, it is recommended to use DNP3 encapsulated in a secure transport protocol. This could be TLS
Conclusions
This article has presented the DNP3 protocol and the functions that can be performed through it. In addition, we have also looked in depth at the security of this protocol, addressing both the critical functions and vulnerabilities of the protocol. As a last point, a series of recommendations in order to achieve secure communication over DNP3.
InprOTech and the DNP3 Protocol
If this article has piqued your interest or you would like to learn more about how to ensure security in the DNP3 protocol in your company, do not hesitate to contact us here. We have a team of experts in advanced industrial cybersecurity solutions ready to help you.
References
[1]Overview of DNP3 Security Version 6
[2] https://ccaps.umn.edu/documents/CPE-Conferences/MIPSYCON-Papers/2019/AllAboutEve.pdf



