Attending RootedCON has become an annual tradition. It is arguably the largest information protection congress in the world, attracting thousands of attendees, featuring multiple venues, and hosting numerous speakers presenting their work across Spain and other locations such as Portugal and Panama.
This year, it will be held in the Kinépolis area of Madrid. We were there on March 7, 2024, to participate in various debates and events, network, and learn about the latest developments in the service provider, solution, and manufacturer communities.
We explored the Madrid Chapter track of ISACA. Vanesa Gil Laredo, President of ISACA Madrid, led the session. It began with an explanation and introduction to the advantages and benefits offered by the international organization ISACA, its activities and objectives, certification, and the services provided by the Madrid Chapter in terms of various courses and certification preparation conferences, CPEs to maintain certification, and more.
In the same room, the roundtable “Cybersecurity and the boardroom, are we speaking the same language?” was held. Given the growing importance of information security management in organizations, dialogue and coordination with the board of directors are increasingly crucial. Speakers included Susana Quintás Veloso (Consultant, Crédit Agricole, and Reale), José Gregorio Parrado Restrepo (Cybersecurity and fraud management expert), Myriam Alcaide Menéndez (Senior consultant and director), and Juan Diego Torres Serrano (National financial manager, Encore Capital Group), discussing the importance of cybersecurity as a cornerstone for achieving strategic business objectives.
Next, we headed to Room 19 to attend the talk “The Legend of the 5 OTs” by David Conde and Guillermo Almagro from the S21Sec DFIR department. OT attacks have increased in recent years, especially from IT networks. Insiders are the main threat, and the lack of information, visibility, and data are common threads, complicating analysis and necessitating the use of asset inventories and anomaly detection tools like Inprotech Guardian.
During the roundtable “Types of cyber incidents in different institutions,” the discussion focused on the challenges faced by various public and private organizations, personal responsibility, and the lack of bureaucratic mechanisms in public administration to respond to incidents, where even the smallest expenses are notoriously subject to regulated, procedural approval processes and timelines, clashing with the urgency of a serious cyber incident.
Furthermore, they believe it’s necessary to increase awareness and comply with national and international security standards and regulations (ISO 27001, TISAX, ENS, etc.) or, given the current volume of attacks, attempt to automate responses with solutions.

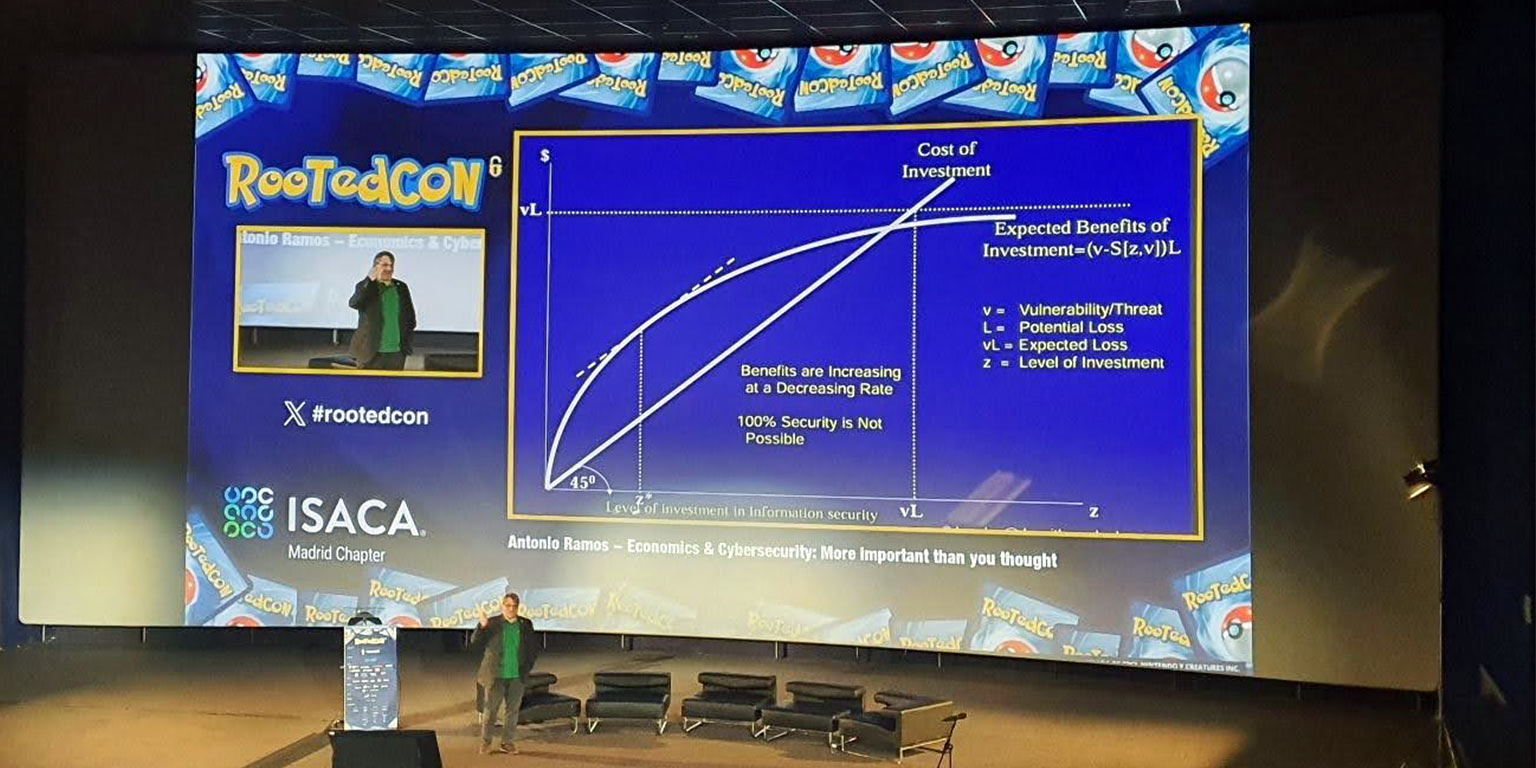
We concluded the morning with a presentation by Antonio Ramos from the security certification body LeetSecurity, “The Economy and Cybersecurity: More Important Than You Think.” In the afternoon session, we headed to Room 25 for the presentation “Dark Sphere: Paralyzing an Entire Country’s Railway Network” by Gabriela García and David Meléndez from Innotec Security, who will show us the key fundamentals such as critical infrastructure levels and why railway transport is particularly vulnerable to OT attacks.
Finally, to end the day, we returned to the ISACA track in Room 17 for the roundtable “Promises and Dangers of the Artificial Intelligence Revolution.” Ricardo Moya (Artificial Intelligence and Technology at Telefónica), Ana De La Torre (Data Scientist at a German multinational), José Miguel Cardona (Auren), Elena García (CISO at Indra), and David Sandoval (Artificial Intelligence and Networking at NTT and Francisco de Victoria University) explored the benefits, challenges, and concerns of using artificial intelligence in cybersecurity and business.



