In an increasingly interconnected world, where cyberattacks threaten not only information but also critical infrastructure, the need for innovative defense strategies has become essential. Among them, honeypots—systems designed to simulate vulnerabilities and attract potential attackers—have become a key tool in the fight against digital threats. Although their use began in Information Technology (IT) environments, their evolution into the realm of Operational Technology (OT) marks a crucial step in protecting industrial systems.
In this article written by Jaime Souto, R&D developer at InprOTech, a general overview is provided on what honeypots are, how they are classified, and, most importantly, how they adapt to the demanding environment of industrial networks, where any breach can have serious physical consequences for society and the environment.
Inception and Definition
In 1986, during the last verses of the Cold War, Clifford Stoll, an astronomer turned sysadmin working in the Lawrence Berkeley National Laboratory, exposed and discovered the hacking activities of Markus Hess, a West German student who was selling information to the Soviet intelligentsia. After learning about the unauthorized access, Stoll and his then-girlfriend Martha Matthews came up with a plan to catch the intruder: to leave a load of dull government documents and directives, slightly modified to look like military classified data, and named SDInet (after Reagan’s Strategic Defense Initiative), enticing enough to catch the hacker’s attention and to keep them busy while the connection was being traced. The trap worked, leading to Hess’ arrest by the German authorities and trial in 1990.¹ ²
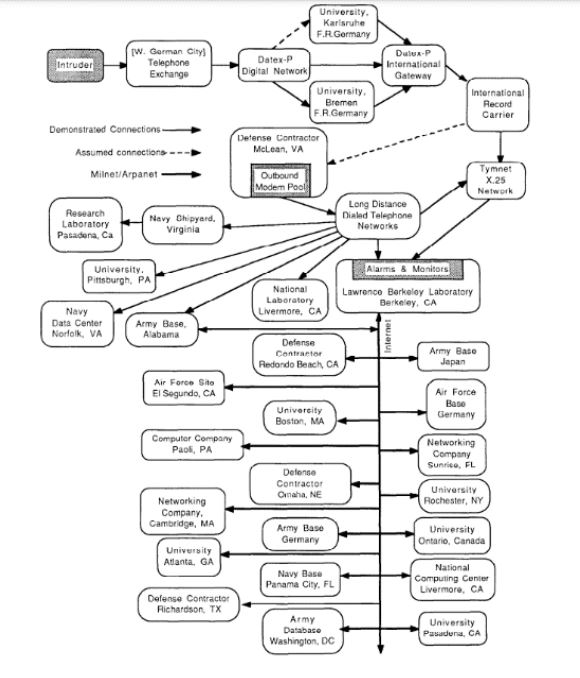
This was the first known occurrence of a honeypot, a cybersecurity device set up purposefully vulnerable to either lure attackers in or to serve as a decoy. Nowadays a mature and classic technique, honeypots are also organized in networks, the so-called honeynets, to better simulate a production environment. ³
Honeypot Classification
Honeypots can be classified following different metrics.
- By purpose: as aforementioned, a honeypot can have two main motivations. We can talk about a research honeypot: by letting the attackers in, a honeypot administrator can learn about the techniques used by nefarious users, and monitor their patterns in order to better enforce the security of the legitimate system. There are also production honeypots, that divert the attention of a hacker from the actual critical network, letting them think that they have actually managed to access.
- By interactivity: depending on the level of “realness” of the system contained in the honeypot, one can classify them by interaction levels. High-interaction honeypots will mimic the structure and services of an actual system, with apparently legit data and functions within. They are rather expensive to set up in terms of resources, but attackers will have a much harder time detecting that they are dealing with a fake system. On the other side of the interactivity spectrum we have low-interaction honeypots, where only the basic structure of a generic operating system will be placed. Much simpler and easier to maintain, but trespassers will quickly reckon that they are in a honeypot (and might use that information to retaliate).
- By role: another classification that interlocks with interactivity is the role of the honeypot. The ones described before are called server honeypots, passive entities waiting for attackers, but one could also set up a client honeypot, an active service like a web browser intended to find, interact with, and learn about malicious or unsecure servers or hosts.
Other types of interesting honeypots are database honeypots, false tables vulnerable to SQL injection, email honeypots used to attract and collect spam, and spider honeypots, prepared to detect bots like web crawlers.
Honeypots in OT systems
As in pretty much every aspect of cybersecurity, honeypots were first used in Information Technology (IT) systems. However, the ever-growing pressure that Operational Technology (OT) systems are experiencing since 2010, when the Stuxnet worm infected an Iranian nuclear facility, is read today as a call-to-action to fortify industrial systems against cyberattacks.
But since the realms of IT and OT are very different, those techniques used in the former need to be revisited in order to be of any use for the latter, and honeypots are no exception. In particular, industrial systems ought to be extremely resilient: any impact on a critical infrastructure of industrial nature, such as energy production or water treatment facility, can have a huge impact on the physical world and on the wellbeing of entire human settlements or other ecosystems.
This means that extra care has to be placed in a correct segmentation of the network to prevent potential leaps of the attacker from the honeynet to the actual system that we need to protect. Moreover, the structure of OT networks tends to be less structured and less predictable, which leads to a higher workload in order to simulate a quality high-interaction honeypot that can deceive attackers.
This can be a really exhausting task, since some search engines like Shodan⁴ greatly simplify the task of discovering whether a service is indeed a honeypot, unveiling the trick. Some researchers even reported their surprise when they noticed the large number of OT systems that were unnecessarily connected to the Internet, often with deficient security implementations. ⁵
As explained in Ref. 6, we can talk about three generations of honeynets.
Generation I (1999) was composed of a firewall and an Intrusion Detection System (IDS), with single honeypots behind. Although it worked well as a log collector, it was very transparent for the occasional intruder.
Generation II (2002) improved the gateway, that now features an IDS sensor and an inline firewall operating as an invisible layer-two bridge. Because of that, there are no time-to-live decrements or MAC addresses for the intruder to play with. ⁷ Another capability is the ability to capture data from the attacker, sniffing their packets. Note that before these developments, a honeypot was not secure enough to be implemented in OT systems.
Generation III (2004) included several deployment and management improvements, deepening on the data capture mechanisms. ⁸
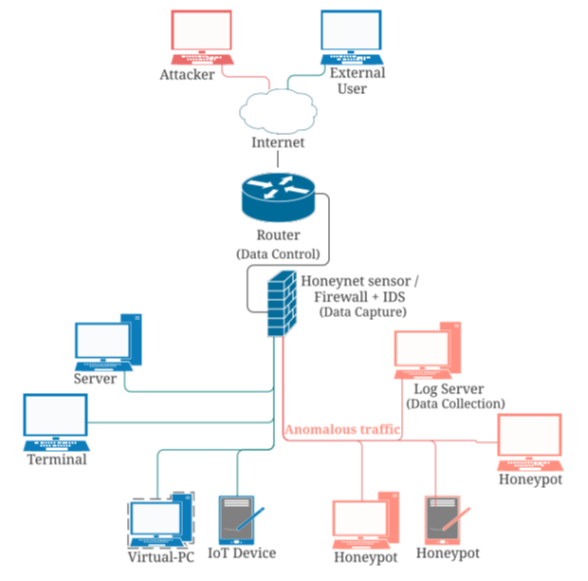
Following, we list several projects that have tackled these problems, each with their own strategy and tailored for different systems.
- Conpot: ¹⁰ one of the most popular OT honeynets, it is a low-interaction and open-source, hence easy to deploy and customize. Supports the main OT protocols (Modbus, S7comm) and also other protocols such as HTTP or FTP. Integrated under the Honeynet Project
- GasPot: ¹¹ Also open-source, it was designed to mimic a Guardian AST gas-tank-monitoring system.
- Gridpot: ¹² Open-source project that simulated an SCADA from an electric grid.
In 2016, Piggin and Buffey shared a detailed report13 on an implementation of a high-interaction OT honeypot developed in 2014, with details about the actual construction of the system, its components and how to make it attractive to intruders. Interestingly, they listed the types of attacks registred by the honeypot:
- A password attack using default vendor credentials against an SCADA.
- An attempt to execute malicious code.
- Dictionary attacks.
- Brute force attacks over ssh.
- A focused attack against a PLC.
- An attempt to disrupt PLC data communications.
Unsurprisingly, the bulk of the attacks were automated reconnaissance scanning.
USA, China and the UK were, by this order, the greatest source of connections, and HTTP was reported as the most common protocol, followed by Remote Desktop Protocol. The authors also highlighted the extra steps taken by the attackers to hinder the localization of their connections, via proxies, VPN and TOR networks.
They repeated the experiment in 2018¹⁴, and their findings perfectly reflect the known trend of increasing risk over OT systems. They found a one-hundred fold growth in the activity, and that the interactions involving the Modbus protocol, now exposed in this study, were clearly intentional. Attacks came from all over the world, with only a portion of them easily attributed to researchers and universities. They did not find, however, any attacker reading or writing process data.
HoneyPot in InprOTech Guardian
Our comprehensive security service for corporate networks, InprOTech Guardian, includes a low-interaction honeypot specifically designed to attract and log malicious access attempts without compromising the security of real systems. If you want to learn more about how it works, you can check it out by reading this article.



