Abstract– TISAX is an information security standard developed by the Association of the German Automotive Industry (VDA) for the evaluation and secure exchange of information between companies in the automotive industry.
The objective of this technical article is to deepen in the objective, scope and benefits that TISAX brings to the industry, to synthesize the main points to consider of the TISAX handbook (reference and structured framework for the assessment and audit of information security in this field), as well as to establish a comparison between the information security management system proposed by TISAX versus ISO 27001.
Introduction
The VDA (Verband der Automobilindustrie) [1] is the Association of the German Automotive Industry. It is an organization that represents the interests of the sector in the country, and is dedicated to promoting the development and competitiveness of its automotive industry, as well as fostering cooperation between automakers, suppliers and other related players. The association also facilitates collaboration and knowledge sharing among its members through working groups, committees and events.
The TISAX (Trusted Information Security Assessment Exchange) standard [2] was launched by the VDA in May 2017. It was created as a framework for assessing and ensuring information security in the automotive industry.
For the implementation of TISAX, the VDA relied on ENX (European Network Exchange) [3]. This was founded in 2000 as a non-profit organization by several European car manufacturers, including BMW, DaimlerChrysler, Renault and Volkswagen. Its main objective was to establish a secure communication platform for the exchange of confidential information in the automotive supply chain.
Thus, TISAX is an information security standard developed by VDA for the automotive industry. VDA-ISA (“VDA Information Security Assessment”) is their assessment framework used, and ENX is an organization that facilitates the secure exchange of information associated with assessments (among other things) in the automotive supply chain.
Benefits
TISAX (Trusted Information Security Assessment Exchange) assessments offer several advantages and benefits for both the organizations that perform them and the automotive industry in general. Some of these advantages are:
- Requirements compliance: TISAX assessments help organizations comply with the information security requirements established by the automotive industry. By obtaining TISAX certification, companies demonstrate their commitment to protecting confidential information and meet the security standards required by automakers and other business partners.
- Trust and credibility: TISAX is recognized and endorsed by the Association of the German Automotive Industry (VDA), which provides greater trust and credibility to certified organizations. TISAX certification indicates that an organization has been independently assessed and has met the required information security standards.
- Improved information security: TISAX assessments help organizations identify and address information security vulnerabilities and risks. This enables them to implement more robust security measures and controls, which in turn improves the protection of sensitive information and reduces the risk of security breaches.
- Collaboration and supply chain access: TISAX certification enables organizations to access and collaborate with automakers and other business partners in the automotive industry. Many automakers now require their suppliers to demonstrate TISAX compliance to ensure the secure exchange of confidential information and guarantee data protection.
- Internationally recognized standard: TISAX is based on ISO/IEC 27001 [4], which makes it widely recognized and accepted in the global information security community. This facilitates interoperability and cooperation between organizations in different countries and strengthens security throughout the automotive supply chain.
Summing up, TISAX increases security, standardization and trust between partners. In addition, it reduces costs by avoiding duplicate assessments by different actors, as the result of assessment audits can be made public on the ENX portal.
TISAX Handbook
The Handbook is the guide of reference for managing TISAX assessments. It describes the steps an entity must follow to pass the TISAX assessment and to share the assessment result with its partners.
The current version of the document is 2.3 as of January 2021, and is available in English, French, German and Chinese, as well as Spanish, in PDF and downloadable HTML.
If a partner requests us to demonstrate a predefined level of information security in accordance with the requirements of the VDA Information Security Assessment (ISA), the 3-step TISAX process must be followed to respond to such a request:
Registration
This involves registering as a participant in the ENX portal, either as an active participant (assessed) or passive participant (receives the result of the assessment). An organization can play both roles simultaneously.
Subsequently, the contractual documentation of the ENX portal and with the authorized audit provider is signed.
Another fundamental step at this stage will be to determine the scope, a concept defined in a similar way to ISO 27001. In this case, a standard (recommended) or customized (extended or reduced) scope is established. In addition, it is necessary to indicate which locations are subject to assessment. There are advantages and disadvantages of a multi-site assessment: on the one hand, resources and costs are saved, and a single due date is obtained by aggregating locations; but in the event of a partial negative result, it will affect the entire exercise, and it will have to be repeated in its entirety.
The assessment objective is also defined at this point, which determines the applicable requirements to be met by the information security management system (ISMS). This is the so-called “TISAX label”, once the audit is passed.
One, or more than one, can be selected:
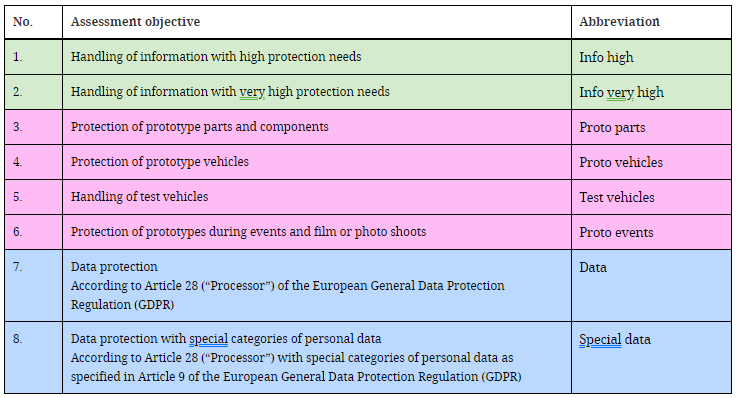
The evaluation objectives have dependencies among themselves. In addition, if several types of information are handled, different levels of protection may be required in each case (normal, high or very high):
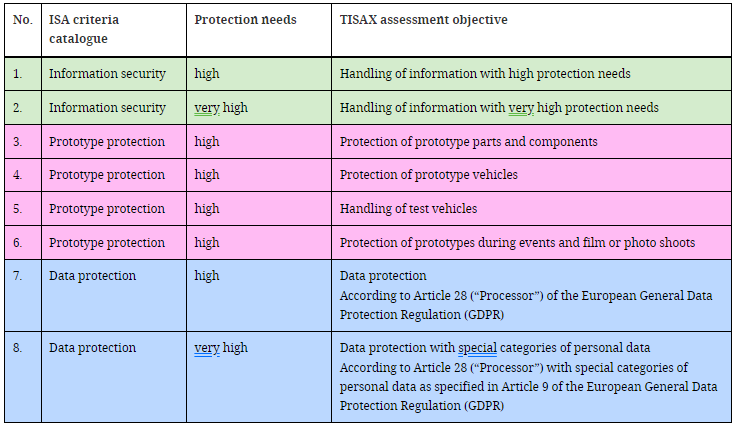
On the other hand, the higher the level of protection required, the more demanding the level of evaluation:
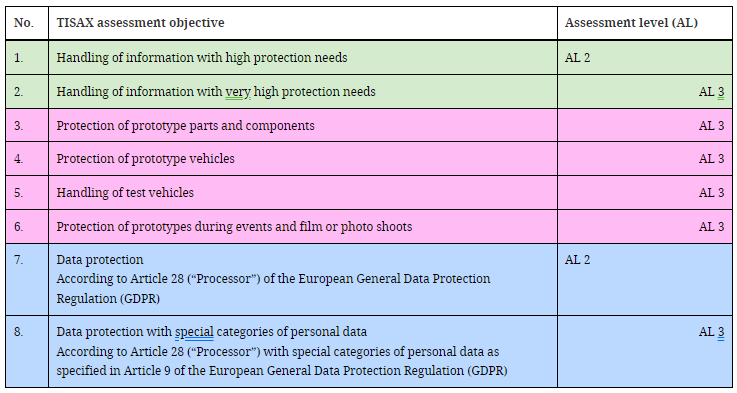
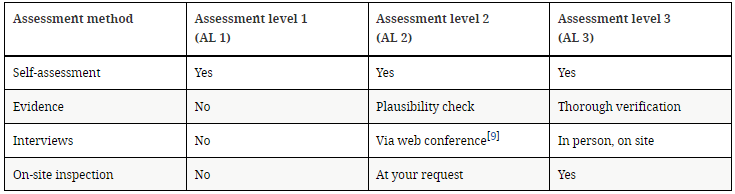
The AL1 level corresponds to a self-assessment, in which the auditor only reviews a template filled in by the active participant. They are not used in TISAX, since they do not award a label.
Level AL2 requires exhaustive verification of the plausibility of the self-assessment: by collecting evidence, through interviews, etc., but without the need to go to the locations in person.
In AL3, the same is verified as in AL2 but more thoroughly, by conducting an on-site inspection and face-to-face interviews.
In addition and to close this stage, the TISAX handbook refers to the payment of the mandatory fees, and the process of registration and use of the ENX portal throughout the process.
Evaluation
This is the core stage of the process. The handbook explains how to use the ISA self-assessment Excel template to check readiness for the formal audit (i.e. internal audit), how to choose an authorized audit provider for the external assessment leading to the TISAX label(s), and the outcome of the process.
The “Information Security Assessment” (ISA) is a catalog of criteria published by the German Association of the Automotive Industry (Verband der Automobilindustrie e.V., VDA). It is the automotive industry standard for information security assessments. Its current version is 5.0.3.
First of all, it must be understood that there are three criteria catalogs:
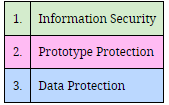
The evaluation objectives, in turn, are related to the criteria catalogs:
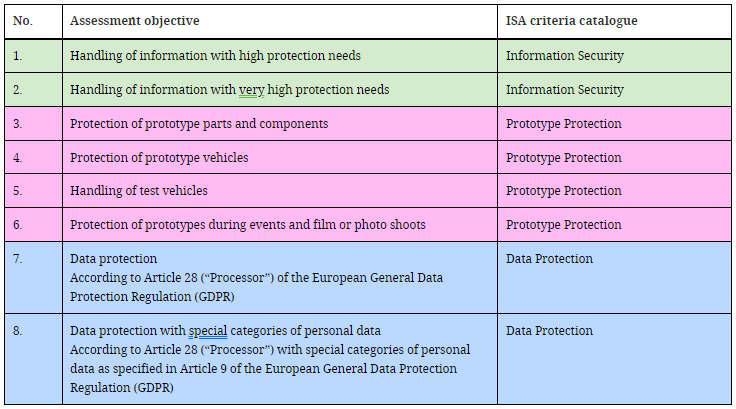
And in the same way, there is another table that relates the applicable requirements of the Excel VDA-ISA to each assessment objective:
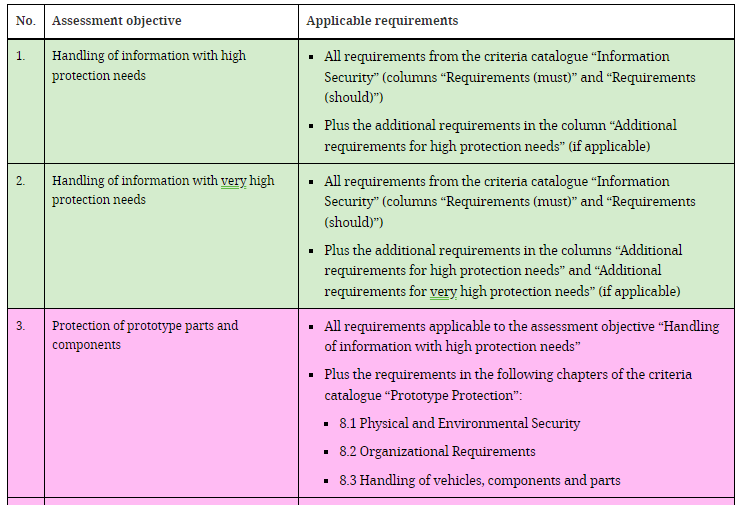
In the Excel template, each criteria catalog groups the questions into chapters based on the different aspects of the information security management systems. The questions for each catalog of criteria or controls are found in the document itself, leaving blank fields for the auditor to carry out the assessment.
The requirements in the template are divided into mandatory, optional, necessary to achieve a high level of protection, or for a very high level of protection. Those necessary for the established assessment objective must be satisfied (see figure 2).
The ISMS aspects are evaluated in terms of maturity on a scale of 6 levels:
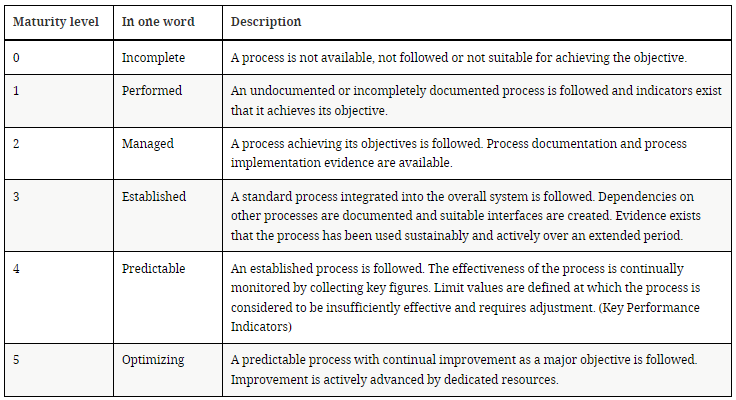
In the self-assessment template, all the levels associated with the applicable requirements must be filled in. The overall maturity level is the average of all target maturity levels (at the question level), altered by the fact that requirements that do not apply do not compute, and that the actual maturity levels are reduced to the target if exceeded.
If the final score calculated by this algorithm is less than 3.0, the ISMS will most certainly need to be improved. If a score of less than 10% or 30% deviation from the maximum is obtained, the assessment will be non-compliant with minimal/significant deviation, respectively.
Once the internal audit has been approved, an authorized supplier must be selected for the formal assessment. The cyclical process in 4 steps is as follows:
- ISMS preparation (internal)
- External assessment (external audit)
- Resolution of non-conformities (internal)
- Verification of remediation (external audit).
Thus, from the point of view of the external auditor, there are three types of audit: initial assessment, assessment of the corrective action plan, and follow-up assessment (the last two may not exist).
The evaluation period for obtaining TISAX labels will last a maximum of 9 months.
An assessment may be compliant or non-compliant. For the purposes of the evaluation result, anything below full or ideal conformity will be referred to as a “finding”. TISAX distinguishes between four types of findings:
- Observation
- Room for improvement
- Minor non-conformity: applies when the non-conformity does not affect the overall effectiveness of your information security management system and does not create a significant information security risk.
- Major nonconformity: applies when the nonconformity raises concerns about the overall effectiveness of your information security management system or creates a significant information security risk.
Only the two nonconformities are findings relevant to the outcome of the assessment.
If the overall result of the assessment is “non-compliant with minimal deviation” and there is a corrective action plan assessment report, temporary TISAX tags will be received, and a subsequent follow-up assessment should be performed.
Finally at this stage, it should be noted that each TISAX assessment has a unique ID in ENX, and the associated report is updated and issued after each assessment (whether initial, corrective action plan, or follow-up).
In addition, the TISAX labels awarded are the product of the TISAX assessment process, summarize the outcome of the assessment and are confirmation that your information security management system meets a given set of requirements. In general, they are valid for 3 years.
Exchange
This section of the TISAX handbook describes how to share the assessment result with a partner and submit the requested evidence.
This is done through the ENX portal, provided the indicated prerequisites are met (documents transferred, and fees paid).
The publication or disclosure permissions are irrevocable, and are valid for the period of validity of the TISAX evaluation. There are five levels of disclosure (the higher the level, the more detail provided to the passive participant):
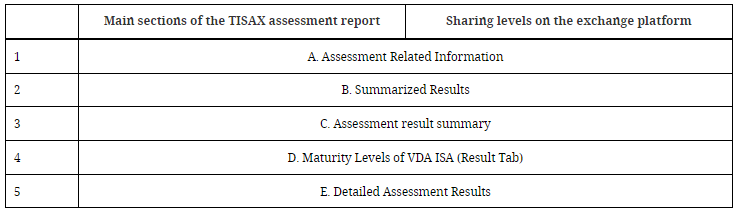
It can also be shared with specific stakeholders with a more comprehensive (detailed) level of information.
TISAX vs ISO 27001
The main differences between ISO 27001 and TISAX (Trusted Information Security Assessment Exchange) are in their scope and specific approach to the automotive industry.
- Scope: ISO 27001 is an international information security standard that applies to organizations in any sector or industry. It provides a general framework for establishing, implementing, maintaining and improving an information security management system (ISMS), and its scope is dynamic. In contrast, TISAX is an automotive industry-specific standard, developed by the Association of the German Automotive Industry (VDA), which is used to assess and ensure information security in the automotive supply chain. Its scope is fixed.
- Specific requirements: While ISO 27001 establishes general and broad requirements for an ISMS, TISAX focuses on the information security aspects relevant to the automotive industry. TISAX includes additional specific requirements and recommendations that are relevant to organizations that collaborate with automotive manufacturers and other automotive companies, such as those related to the protection of prototypes.
- Recognition: Although ISO 27001 is a widely recognized and internationally accepted standard in various sectors, TISAX has been developed and endorsed by the Association of the German Automotive Industry (VDA). TISAX is specifically recognized by the automotive industry and is required by many automotive manufacturers as part of their information security requirements for their suppliers, becoming a block to doing business with many of them.
- Assessment process: Both follow a similar audit-based assessment process. However, TISAX uses the VDA-ISA (VDA Information Security Assessment) assessment framework as its specific approach, with assessment objectives and levels and a related requirements catalog. ISO 27001 faces the problem completely differently: the customer defines the scope, and must consistently select which security controls will or will not apply in their particular environment in a statement of applicability (SOA).
In TISAX, the approach is compliance based on maturity levels and the risk analysis is derived from the VDA-ISA working group, while in ISO it is ON/OFF and the risk analysis is based on the particularities of the company.
Finally, in ISO it is the certification body itself that issues the certificate, which is valid for 3 years and requires annual periodic audits; TISAX, on the other hand, issues the labels and exchange registers, which are valid for 3 years, without the need for intermediate periodic actions.
De todo lo anterior se deriva que las evaluaciones TISAX y las certificaciones en base a ISO 27001 presentan ciertas similitudes pero no son equivalentes. A una organización certificada/evaluada bajo uno de los estándares se le allanará el camino para alcanzar los requerimientos del otro, pero en modo alguno es un proceso automático o trivial, por lo que se recomienda acudir a proveedores de servicios de consultoría especializados como Inprosec/InprOTech.
Conclusions
An introduction is provided to TISAX (Trusted Information Security Assessment Exchange), an information security standard developed by the Association of the German Automotive Industry (VDA). The benefits of TISAX assessments are highlighted, including compliance, trust and credibility, improved information security, supply chain collaboration and access to business opportunities in the automotive industry.
The paper summarizes the main features of the TISAX Handbook, which provides guidelines and requirements for information security assessments in the automotive industry, based on the ISO/IEC 27001 standard but with a specific focus on aspects relevant to the automotive sector.
Key differences between TISAX and ISO 27001 are also highlighted, such as the automotive-specific scope of TISAX, additional requirements relevant to the automotive sector, the automotive industry’s endorsement of TISAX and the use of the VDA-ISA assessment framework in TISAX.
Overall, the document helps to understand the importance and impact of TISAX on information security in the automotive industry.
REFERENCES
[1] VDA. https://www.vda.de/en
[2] TISAX handbook. https://www.enx.com/handbook/tisax-participant-handbook.html
[3] ENX portal. https://portal.enx.com/en-US/#
[4] ISO 27001:2022. https://www.iso.org/obp/ui/#iso:std:iso-iec:27001:ed-3:v1:en



