The National Institute of Standards and Technology (NIST) is an agency of the United States Department of Commerce. It was founded in 1901 under the name of the National Bureau of Standards (NBS) with just a metrological task such as the custody of the physical objects embodying the standards for the kilogram and the meter, or the development of measuring instruments for electricity and light. Over the years its mission shifted towards technological development following the war campaigns of the first third of the 20th century until in 1988 the agency was renamed NIST with the official mission of “promoting innovation and industrial competitiveness in the United States by advancing measurement science, standards and technology to improve the economic security and quality of life of Americans.”


Part of this task is the publication of research and standard guides and procedures such as this NIST SP 800-82 dedicated to establishing the bases for cybersecurity of Industrial Control Systems (IDS) and which is, de facto, the reference text in this matter. Its first version was published in May 2013, a few years after the Stuxnet worm made crystal clear that it was the time to proactively secure networks and industrial complexes. This text quickly became obsolete and in May 2015 a second improved and expanded version emerged. Currently, a third version is published in review format, awaiting the consolidated publication with the contributions made from the community in April 2022.
In this article we will briefly summarize the contents of NIST SP 800-82 and discuss the updates to the latest version, NIST SP 800-82r3.
Summary of NIST SP 800-82
The main object of study of this document is, as mentioned above, ICS or Industrial Control Systems. Among the most typical components of ICS are SCADAs (supervisory control and data acquisition) systems, DCSs (distributed control systems), and PLCs (programmable logic controllers). They are typically found within industrial environments: electricity, water, refineries and gasification, transportation, chemical, pharmaceutical, paper and pulp, food and beverage, and discrete manufacturing (automotive, aerospace, durable goods), and form the functional core of critical infrastructures, highly interconnected and mutually dependent systems that are considered essential for the functioning of an industrialized society. Therefore, they are elements highly protected by these societies’ states and governments. In the United States, 90% of critical infrastructures are owned and managed privately, but federal agencies also manage many critical ICS, such as Postal Service or air traffic.
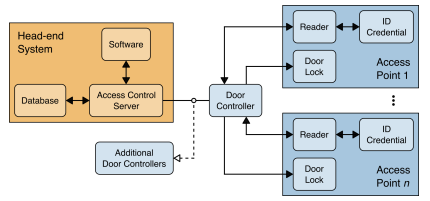
The ultimate objective of this NIST special publication is to summarize typical IC topologies, identify common threats and their vulnerabilities, and provide security recommendations to address the associated risks.
An important point to establish is the main differences with traditional IT (Information Technology) since its cybersecurity standards are much more mature. Traditionally, ICS were systems whose main protection was by isolation (air gap) and in which, by operating with proprietary control protocols and hyper-specialized software/hardware, they managed to keep potential attackers at bay. In recent years, the unstoppable trend is to reduce this isolation due to the introduction of the Internet Protocol for communication within networks and the integration of industrial networks with the rest of the company’s management systems, opening the possibility of more incidents and cybersecurity vulnerabilities. Furthermore, communications are increasingly tending to be wireless, so just physical proximity to the network (not physical access) would be necessary to disrupt the system. Many of the solutions implemented to solve these problems in IT are not suitable for ICS.
Another fundamental difference with IT is the interaction with the material world, practically nonexistent beyond the use of printers. This translates into a potential risk for the physical integrity of the people present in the plant in the event of failures or incorrect operations, as well as for the environment. Furthermore, general ICS priorities (namely: Availability, Integrity, Confidentiality) can and often do clash with IT priorities.
Threats to ICSs can come from many sides: hostile governments, terrorist groups, disgruntled employees, malicious intruders, complexities, accidents, natural disasters, destructive actions from within. Some examples of incidents that could be encountered in an ICS are: blocked or slowed traffic; unauthorized changes in instructions, commands, alarm thresholds that could damage, misconfigure or shut down equipment; modification of traffic sent to operators; modified settings, virus and malware in general; interference with other systems on the network.
The main objectives in an ICS implementation would be those listed here:
- Restrict logical access to the ICS network.
- Restrict physical access to the ICS network.
- Protect the individual components of the ICS network: up-to-date security patches, ports and services, user roles, log review.
- Restrict unauthorized modification of data, both traffic and memory.
- Detect security events and incidents.
- Maintain functionality during adverse conditions.
- Restore the system after an incident.
The importance of having a human team focused on ICS cybersecurity is highlighted, compose at least of: IT, control engineer, control systems operator, network and systems security expert, a management member, member of the risk prevention team.
To finish with this small summary, the points that the defense strategy of an ICS should have are detailed, which we will only list here:
- Development of security policies and procedures based on the Homeland Security Advisory System threat system.
- Preparation of training material applied specifically to ICS.
- Follow the security of the systems based on their life cycle, from architectural design, installation, maintenance, and confiscation.
- Implementation of a network topology with several levels depending on the security or level of protection necessary.
- Logical separation between corporate networks (IT) and ICS (firewalls, DMZ, unidirectional access doors).
- Redundancy of critical components.
- Design critical systems taking into account the principle of fault tolerance/graceful degradation (that the system does not break even if some of its parts do).
- Disabling unused ports and services.
- Restriction of user roles and permissions to those strictly necessary.
- Use of separate authentication systems for the corporate network (IT) and ICS.
- Use of modern technology for physical access (e.g. smart cards) to take the initiative against malicious actors.
- Implementation of computer security controls such as antivirus.
- Application of security techniques such as encryption.
- Keeping security patches up to date.
- Review of the logs of the critical areas of the ICS.
- Use of secure and reliable network protocols.
All the points presented in this summary are described in extenso in the original document, with which any professional in the industrial branch should be at least familiar.
3rd review: what’s new
Cover more ground: In the title of the publication we can spot the appearance of the acronym OT, Operation Technology, which encompasses all the systems that come together in the computerized treatment of industrial systems, in which ICS are a leading element but not the only one. Examples are the IIoT (Industrial Internet of Things), the BAS (property automation systems, or building automation), physical access and control systems, the password manager and multi-factor authentication, or the control of the supply chain with respect to supplier interaction.
Risk control and the Zero Trust policy: assumes the acceptance that security incidents are going to occur, and that one must learn to identify and prioritize potential threats and vulnerabilities. In relation to this, the trend in the industry is to build architectures based on the concept of Zero Trust, according to which no device, user, or connection can access resources without passing the corresponding control. OT recognizes the complication of implementing this policy at the lowest levels of the functional organization chart of a factory (HMIs, PLCs), whose protocols are often too particular.
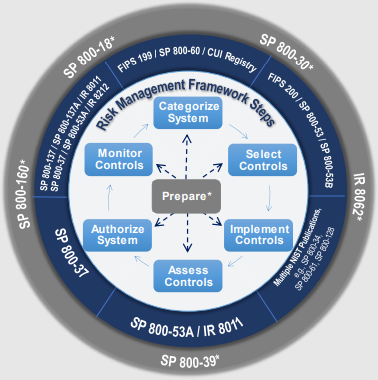
Alignment with other more general NIST standards such as the CSF (Cybersecurity Framework) or NIST 800-53r5, titled Security and Privacy Controls for Information Systems and Organizations. One of the most immediate practical implications is to give more importance to the response plan for a security incident (summarized in the mantra Identify, Protect, Detect, Respond, Recover).
As can be seen from this review, the third revision represents a broad improvement of the contents of the previous version, making the text more autonomous and versatile, and delving into a realistic management of possible malicious or disruptive events. In short, an integration of measures from the IT world, already well established and mature, but conveniently adapted to the OT environment.



