On March 12th, Oscar Iglesias Touceda attended the “A pleno SOC” event in Madrid under the banner of Espacio TISEC.
Under the name EspacioTISEC, the well-known industry magazine SIC organizes in Madrid a series of sessions focused on cybersecurity operations, particularly in the realm of managed service providers (MSSPs) and the services they offer from their SOCs (Security Operations Centers), which organize a significant portion of their monitoring, detection, and incident response capabilities.
The focus will be both technological (advancements, new services, AI impact, etc.) and on legal and regulatory aspects stemming from the conditions and obligations these operators must adhere to under various national or supranational regulations (EU).
Below is a brief summary of the sessions from the “Technologies Aimed at Managed Cybersecurity” part of the program, which we attended due to its relevance to our flagship product, InprOTech Guardian.
Technologies Aimed at Managed Cybersecurity
Talk by Álvaro García
Initially, we heard from Álvaro García, senior sales engineer for Iberia at Crowdstrike.
Álvaro posits that we are facing the second major paradigm shift. Initially, technology was very reactive, with poor protection capabilities and cumbersome software agents. In the first wave, the trend was towards seamless integration, simplification, process agility, and semi-automatic response in many cases with AI, transforming the operational platform into an integrated SOC. The goal is 1-10-60 (incident detection in 1 minute, holistic understanding in 10, and complete response and recovery in 60).
In the second wave, they propose an open platform that can ingest third-party data to enrich analysis capabilities, with enhanced intelligence, and providing an agile response by having a single management interface that incorporates AI to even automate incident reporting for the analyst.
Talk by Carlos Tortosa
Next, we heard from Carlos Tortosa, director of major accounts at ESET Spain.
His perspective involves the need for universal access to cybersecurity, talent, providing usable and simple tools, facilitating prevention, response, and recovery services, as well as compliance with regulatory services and tools.
The philosophy they propose is trust, usability, lightness, and easy deployment, and with this approach, they present their managed security platform, ESET Protect. He primarily values their threat intelligence service, with feeds, among others, of IPs, URLs, and APTs returned in a service format.
Talk by Alberto R. Rodas
Thirdly, we had Alberto R. Rodas, director of pre-sales engineering for Spain and Portugal at Sophos.
Alberto points out the main reasons why attacks are successful, such as human errors in security control configurations, unjustified exceptions, lack of patching, not reviewing detected threats due to lack of staff, etc.
And the bad guys never rest. Ransomware strikes 43% on weekends, and the speed of attacks has gone from about 18 days in 2020 to 5 days in 2024.
His proposal is to centralize detection and response capabilities in a SOC over an XDR service, which can also integrate logs from major competitors, such as Microsoft.
Talk by Miguel Carrero
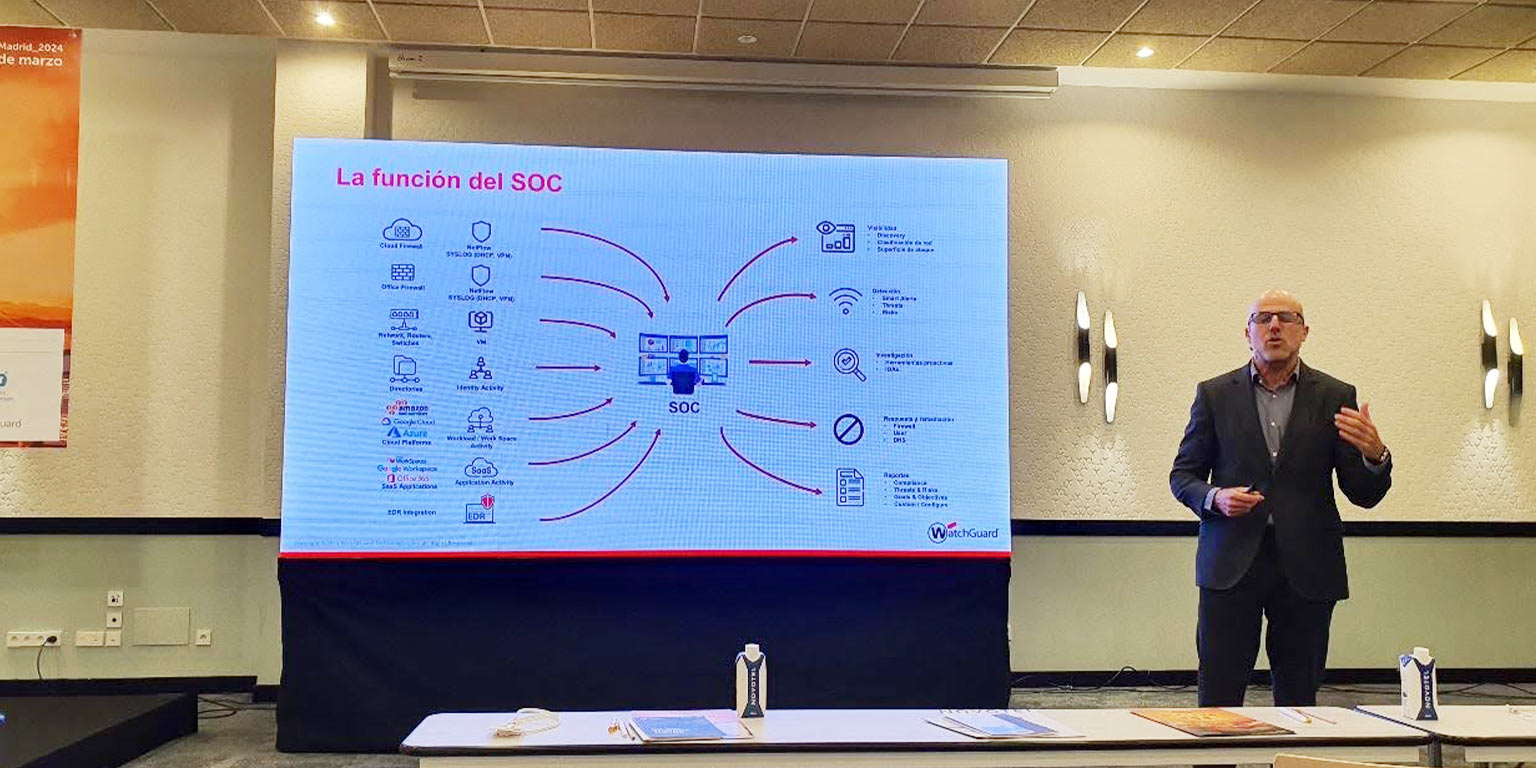
Next, we heard from Miguel Carrero, vice president of secure service providers & strategic accounts at Watchguard.
He reflects on the things that don’t change, and those that do. What doesn’t change is the function of the SOC, and its necessity. He emphasizes the need to investigate incidents with the right tools for effective remediation, reaching back to patient zero. And he argues that the network has changed, evolved. The perimeter can now be in our pocket, on our smartphone.
He acknowledges the financial balance benefits of giving up manual processes. And about NDR solutions (network detection and response), which detect anomalous system behaviors by applying analysis based on various strategies to north-south and east-west network traffic (similar to InprOTech Guardian in a way, since our solution adds more inventory capabilities, detection based on process mining, an intrusion detection system, or external cyber intelligence sources, to give some examples). He highlights in this sense the acquisition of CyGlass in September, which allows them to enhance the network detection and response capabilities based on AI and OpenXDR for WatchGuard, cloud-based and without physical appliances.
Lastly, he mentions that, in the interest of simplification, there is a tendency to use XDR solutions instead of SIEM, given their ease of management versus the need to define and maintain complex correlation rules (eternal balance between security and usability/cost of maintenance). And he argues that telemetry should be based on network traffic, identities, and endpoints.
Debate on Integration, Interoperability, Scalability, and Automation
Finally, to close the session, a debate was held, led and moderated by José Manuel Vera, writer for SIC. The session’s leitmotif is “Integration, Interoperability, Scalability, and Automation”.
They discuss the keys to an effectively functioning MSSP. The reality is that the truth cannot be known until a significant incident occurs. But the approach of a 3-level SOC might be somewhat outdated with modern capabilities, and it might make more sense to categorize by services or technologies. But caution is advised, as SOC services are proliferating like mushrooms, and many are of dubious effectiveness.
Álvaro poses the challenge of whether traditional schemes are really being chosen to justify the budget based on incidents, but the rest of the speakers believe the optimal point between needs and investment must be found, as neither the old ways work anymore, nor is the new a golden hammer that will work effectively 100% of the time.
They later talk about certifications, in which they defend that certifications should be contextualized to the specific service and client, and not generally, including the organization, services, and technology. And there should be advocacy for the unification of criteria and/or certifications at the European level, as the current atomization and disparity of criteria between countries do not seem to make sense, but their usefulness in terms of risk mitigation through proper data, process, and personnel management is clear.
Regarding the mistakes made in SOCs, sometimes it’s a sin to rely on very junior staff, or not to properly balance the needs of that staff and associated expertise, technologies, and processes. There’s also excessive confidence in AI, and the pretense that it allows for the dispensing of human capital, which is not expected to happen, but can indeed give a huge boost to productivity, making what used to take a level 3 SOC operator an hour to diagnose now available in seconds for expert discrimination.
Regarding client tropes, they agree that clients are different and their needs are very specific and different from the competition, when in reality criminals use very similar modus operandi on clients from different contexts. Or the fear of not choosing the right provider. Or that services offering active response might block a legitimate workflow, and that sometimes they delegate management to humans at the beginning, but then with trust (and also due to workload), end up leaving it on autopilot.



